Secure Your DevOps Journey. Continuously
Continus DevSecOps is an All-In-One DevSecOps Solution that consolidates Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and Infrastructure-As-Code Security (IACS) into a single integrated platform. By empowering both developers and security teams, we guarantee the security of every aspect of your software, including source code, third-party components, containers, and APIs, throughout the entire Software Development Life Cycle (SDLC).
Benefits to expect from Us
At Continus, we recognize that conventional security tools are not Devops Friendly and lack compatibility with DevOps practices by offering limited support for modern cloud-native applications.
Below are the advantages you gain by adopting Continus DevSecOps Solution:

Build and deliver secure software
Seamless security integration into developer workflows to secure the build and deployment process without compromising developer experience.

Continuous Assessment
Beyond mere identification, we continuously monitor vulnerabilities and assist in their mitigation, safeguarding your projects.

ci/cd Integration
Adapt security to development workflows to reduce developer friction. Prioritize ease of integration and improved developer experience as much as the effectiveness of the solution itself.

Secure the software supply chain
Secure the usage of both internal and external code dependencies in the software development supply chain.

Measure and monitor technical debt
Avoid compromising code quality and application delivery by proactively measuring and monitoring technical debt at the source code level.

Optimize Budget & Costs
Reduce the costs associated with benchmarking and purchasing multiple tools for each type of assessment by using one unified solution.
Features To Achieve Your Strategic Objectives
We Provide
Detecting Vulnerabilities in Source Code
Securing the source code by analyzing GIT repositories to identify sources of vulnerabilities to be fixed before reaching the production environments
We Provide
Detecting Vulnerable Dependencies
Risk identification in 3rd-party components embedded in your applications and containers
We Provide
API Security
Basic and authenticated scans of your web services and APIs (openapi, graphql, soap) for pentential vulnerabilities
We Provide
Detecting Infrastructure-As-Code Vulnerabilities
Scan Docker, Kubernetes and Terraform for known vulnerabilities and security misconfiguration issues
We Provide
CI/CD Integration
Continus CLI (Command Line Interface) makes it easy to integrate Security Checks and Gateways into developers workflow and build systems such as Jenkins
Why Continus DevSecOps?
Streamlined Workflows
Foster better collaboration between development and security teams, resulting in shared security responsibilities, secure builds and secure deployments.
Cost-Effective
A unified solution means less expenditure on multiple tools. Save both time and money with our comprehensive offering.
Stay Ahead of Threats
With continuous monitoring, remain proactive against potential security threats, ensuring your infrastructure’s resilience. Detect security issues before the evil guys.
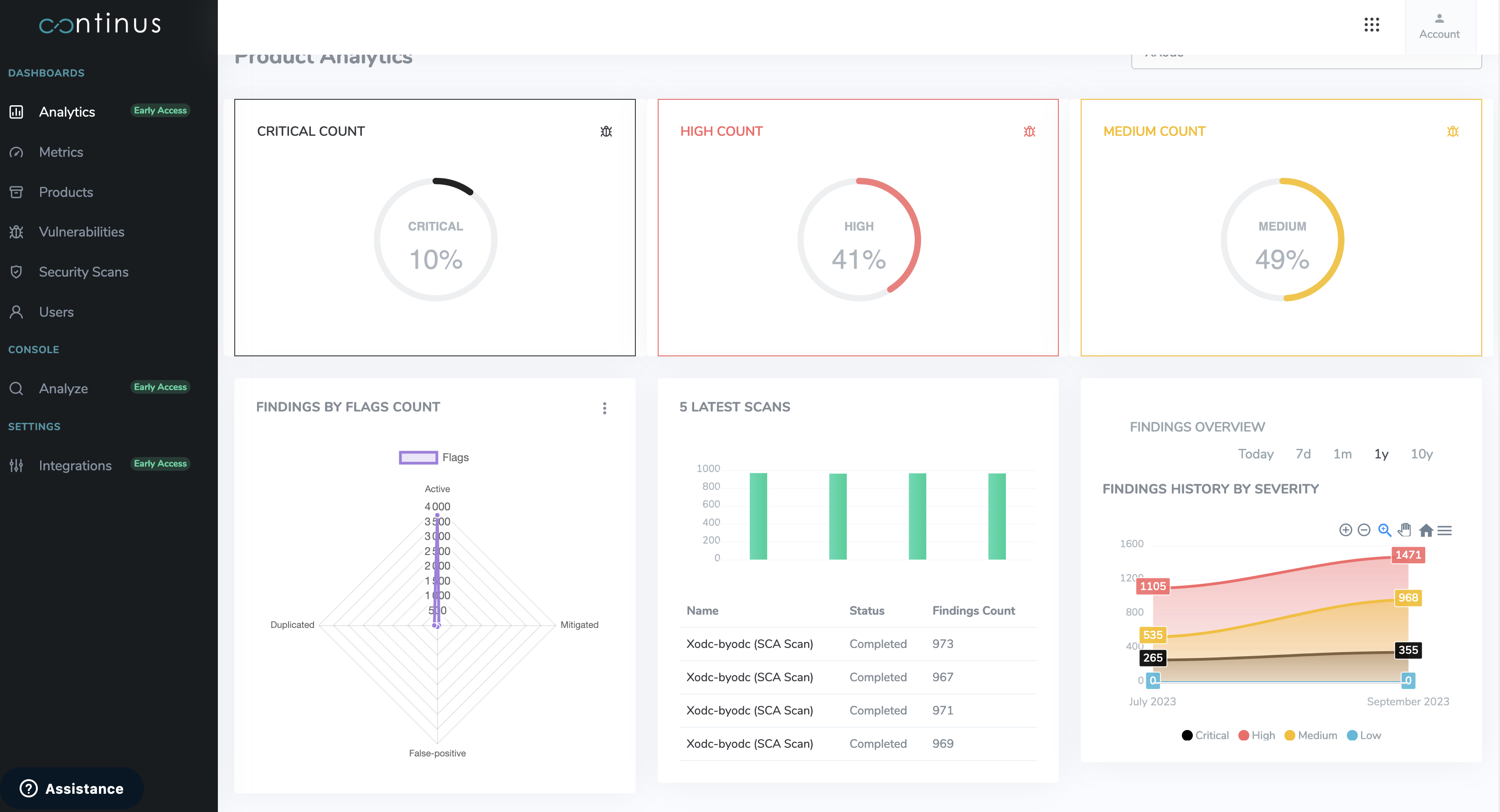
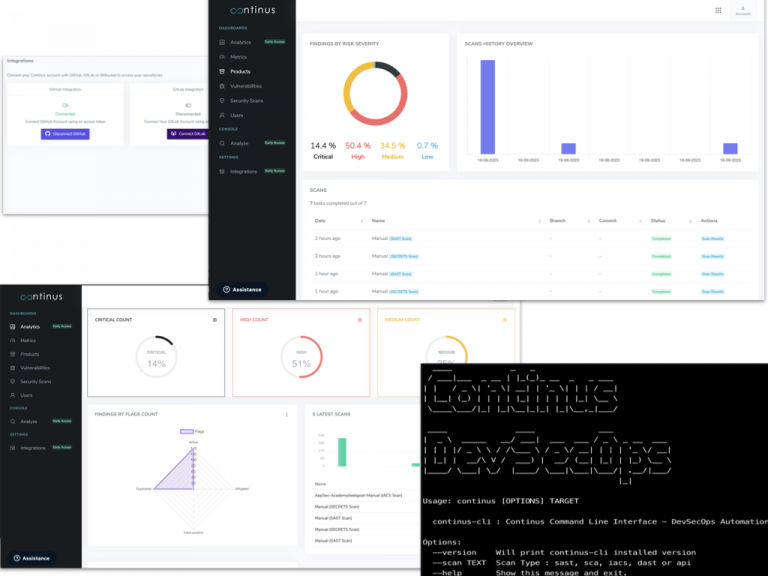
Easy 10-Minutes Setup
DevSecOps processes can often be time-consuming, but not when you choose Continus.io. Get started in just 10 minutes.
We secure thousands of application repositories, thanks to our scalable solution!




Key Use-Cases
DevSecOps Pipeline
Complete your DevSecOps posture and automatically find vulnerabilities in all application layers
Security by design
A single unified platform to manage the security of your applications at every stage of the lifecycle.
security compliance
Saving time for developers and security team with reduced complexity and easier compliance
Continus.io – An Automated DevSecOps solution
Experience end-to-end security for your software supply chain. Integrated within CI/CD or DevOps pipelines, Continus.io manages all crucial security activities during the build and deployment phases, ensuring that new vulnerabilities are promptly reported and rectified.
Continus DevSecOps & Continus.io ©2023, All rights reserved.